How to add a SSL Certificate to Directus
SSL certificates are vital to securing your data by encrypting all traffic between the client and your server. In this article I'll cover how you can add a Let's Encrypt certificate or Paid certificates to Directus. This assumes you are using linux and have root access and have a domain name already pointing to your server.
To add an SSL certificate to Directus you will need a proxy like Nginx, then you can run certbot to generate a certificate. Certbot will automatically add the configuration.
If you haven't already set up Nginx, use my article below to set this up first.

Using Let's Encrypt (Free)
Now that you have Nginx installed and configured, you'll need to set up certbot.
Step 1: Install snapd using the relevant command below.
sudo yum install snapd
sudo dnf install snapd
sudo apt-get install snapdStep 2: Update the snapd core to the latest version by running this:
sudo snap install core; sudo snap refresh coreStep 3: Install certbot using snap
sudo snap install --classic certbotStep 4: Create symlink for certbot in your systems path so it can be run without needing the path.
sudo ln -s /snap/bin/certbot /usr/bin/certbotStep 5: Run the following command to automatically edit you nginx configuration with the paths to the certificates.
sudo certbot --nginxThis command will create a token on your server, then attempt to reach the token from the web address. If valid, a certificate will be created.
Lastly, create a cron job to run the following command daily or weekly to renew your certificate.
sudo crontab -eCopy and paste the line below into the edit then save and close. For this unfamiliar with the vim editor, press ESC to exit the Insert mode, then type :wq (the colon is required). Press ENTER write (w) and quit (q).
0 0 * * * certbot renewThis will try and renew the certificate at midnight every day. The certificate will only renew closer to the expiry date. Running the command frequently ensures it renews before it expires.
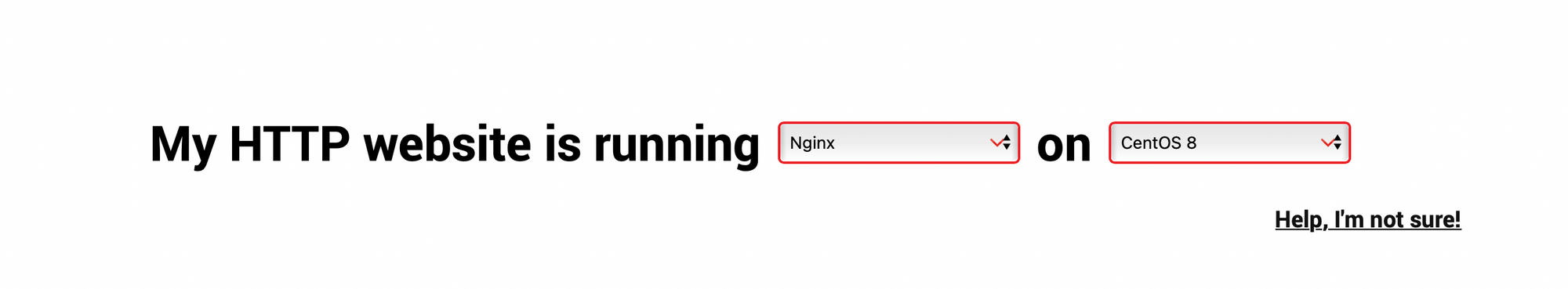
The certbot website has a more comprehensive guide if you prefer.
The intructions are very helpful, all you need to do is select Nginx as the Software and your operating system from the list.
Using Paid Certificates
There are 3 types of certificates, Extended Validation (EV SSL), Organization Validated (OV SSL) and Domain Validated (DV SSL). They all have the same level of encryption, but have different levels of verification. This changes the padlock symbol on your browser from the standard green to a big box with your company name inside. This is very important for enterprise level companies or University's to reassure they are using the official website and not a copycat. If you prefer to pay for a certificate, here are some providers with premium options.
- SSLs.com
- Namecheap.com
- Register.com
- Network Solutions (Enterprise Level Protection)
When you are given your certificates, you need to upload them to your website host. Add them to a memorable location such as /etc/ssl/
It's also worth creating a dhparam file. This makes it significantly harder for hackers to decipher your encryptions if they somehow get hold of your private key.
cd /etc/ssl/
openssl dhparam -out ffdhe4096.pem 4096Here is the recommended Nginx configuration for securing your website. Make sure to change domain.crt and domain.key to your new certificates.
# Certificate(s) and private key
ssl_certificate /etc/ssl/domain.crt;
ssl_certificate_key /etc/ssl/domain.key;
# RFC-7919 recommended: https://wiki.mozilla.org/Security/Server_Side_TLS#ffdhe4096
ssl_dhparam /etc/ssl/ffdhe4096.pem;
ssl_protocols TLSv1.3 TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ecdh_curve secp521r1:secp384r1;
ssl_ciphers EECDH+AESGCM:EECDH+AES256;
ssl_session_cache shared:TLS:2m;
ssl_buffer_size 4k;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
resolver 1.1.1.1 1.0.0.1 [2606:4700:4700::1111] [2606:4700:4700::1001]; # Cloudflare
# Set HSTS to 365 days
add_header Strict-Transport-Security 'max-age=31536000; includeSubDomains; preload' always;Test and restart Nginx to apply changes.
nginx -t
sudo systemctl restart nginxConclusion
You now have an SSL certificate encrypting all you data in Directus. It's important not to share your SSL certificates with anyone and store them safely. If you found this useful, subscribe by adding your email address below and I can share any new articles with you.
Keen to know more?
Check out these SSL/TLS resources on Amazon, there are usually some great deals.